Forget the world of work for a while and build a full sized arcade cabinet complete with clicky buttons joystick and even a coin machine to extort money from yourself.
Bro network security monitor raspberry pi.
A raspberry pi is a small form single form computer developed by the raspberry pi foundation.
Discover raspberry pi portable computing in the latest edition of the magpi.
Sensor install deploy bro ids critical stack logstash and sweet security web admin install deploy elasticsearch kibana and apache arp spoofing full code to monitor all network traffic out of the box without network changes.
To date there have been five different product families produced.
Zeek formerly bro is the world s leading platform for network security monitoring.
Flexible open source and powered by defenders.
The bro network security monitor ships with built in scripts to monitor both dnp3 and modbus traffic.
Web admin install deploy elasticsearch kibana and apache.
This post uses the newest generation termed the raspberry pi 4 b.
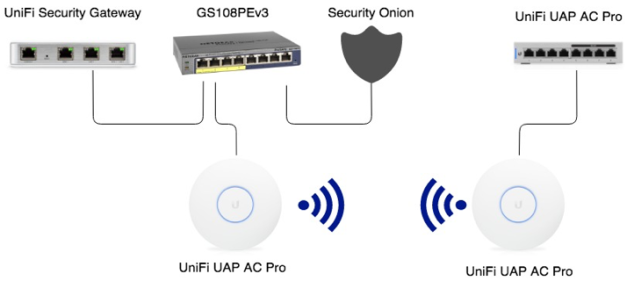
Suitable for a home blackbox deployment it will record everything that happens on your network.
In the continuing quest to install security software on raspberry pi s testing their capacity to be used as small nodes that can be placed here and there on demand the time has come for installing bro.
Sensor install deploy bro ids critical stack logstash and sweet security.
However the atomic pi was recently announced and it s based on the intel atom processor.
Use it to detect threats and or to provide network forensics to a malware lab.
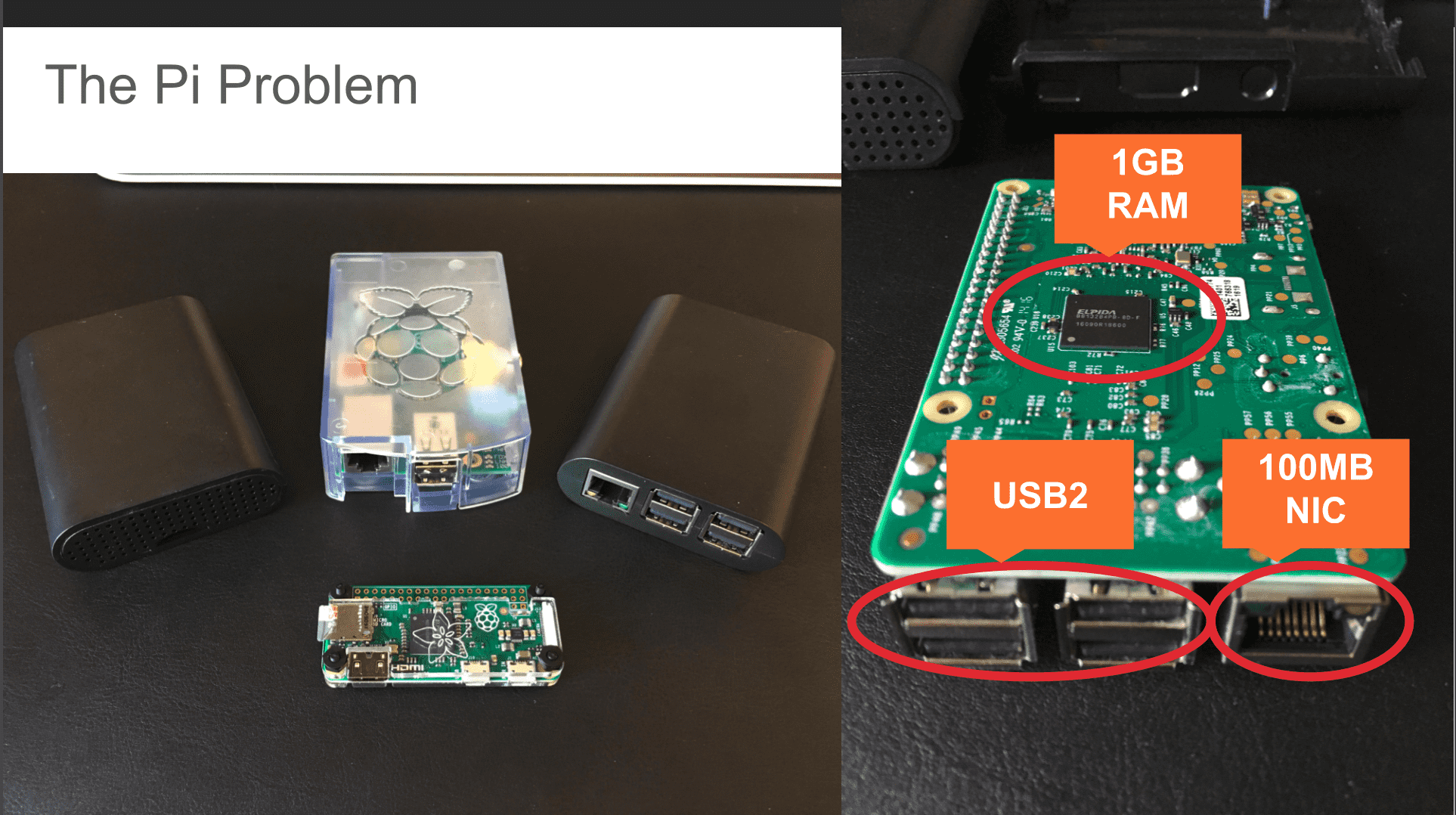
The raspberry pi is simply not powerful enough to do the kinds of things you would want to do with security onion.
Blackbox a raspberrypi 3 nsm network security monitor based on bro netsniff ng loki and critical stack.
The 4 b family consists of three models with varying levels of ram.
Bløgg no installing bro the network security monitor on a raspberry pi posted on 2015 11 01 20 23 by bjorn under uncategorized.
Read it now hackspace issue 35.
Complete bro log support all bro log files are now normalized by logstash.
The magpi issue 98.
The raspberry pi has an arm processor and we do not compile security onion for arm.
What i ve done with a raspberry pi as part of the research into my black hat briefing i found that the bro network security monitor is well suited to detect such attacks.